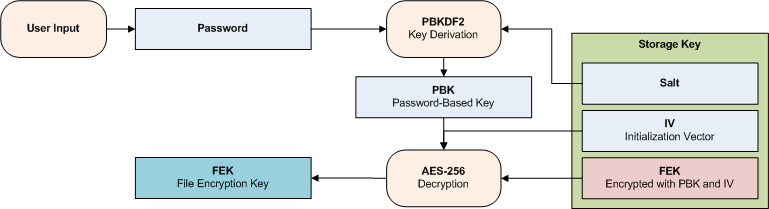
Security aspects of removing a user from an organization or collection - Vaultwarden Forum (formerly Bitwarden_RS)

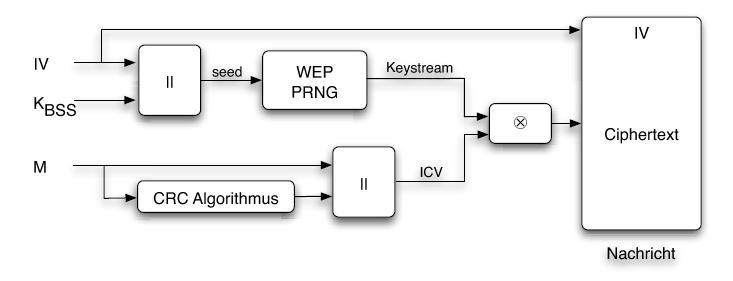
SOLVED: We conduct a known-plaintext attack on an LFSR-based stream cipher. We know that the plaintext sent was: 1001001001101101100100100110. By tapping the channel carrying the ciphertext, we observe the following stream: 10111100001100001001010110001.

SOLVED: We conduct a known-plaintext attack on an LFSR-based stream cipher. We know that the plaintext sent was: 1001001001101101100100100110. By tapping the channel carrying the ciphertext, we observe the following stream: 1011110000110001001010110001.

Cryptopals: Exploiting CBC Padding Oracles | NCC Group Research Blog | Making the world safer and more secure
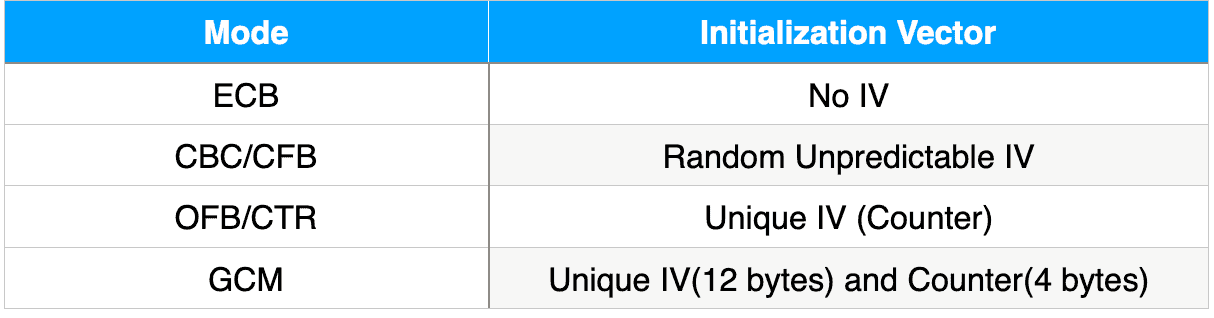
Security Best Practices: Symmetric Encryption with AES in Java and Android | by Patrick Favre | ProAndroidDev